What every experienced APT incident responder agrees on, is the way APT attacks are conducted.
The APT kill chain can be presented with some variations, depending on the detail level you want to show, yet its content is always the same. We chose to show here the easiest kill chain we could draw, not to panic anyone with technical details (yet). We will really go deep into every process of an APT attack in this serie of blog posts, yet we believe it is good to start explaining it from a distant point of view.
Here is a first view, without details, on the APT kill chain:
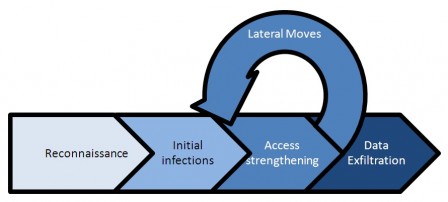
From the victim perspective, the risk evolution can be easily translated from this simple killchain:
![]()
When the data exfiltration is done, the story goes on: the attackers are still there, they stay on the system, connecting to it from time to time, and continuig the access strengthening : checking their backdoors are ok, updating their malware, keeping their high level accesses, and exfiltrating more data. It goes on and on.
This cycle, a bit more explained, can be represented this way:
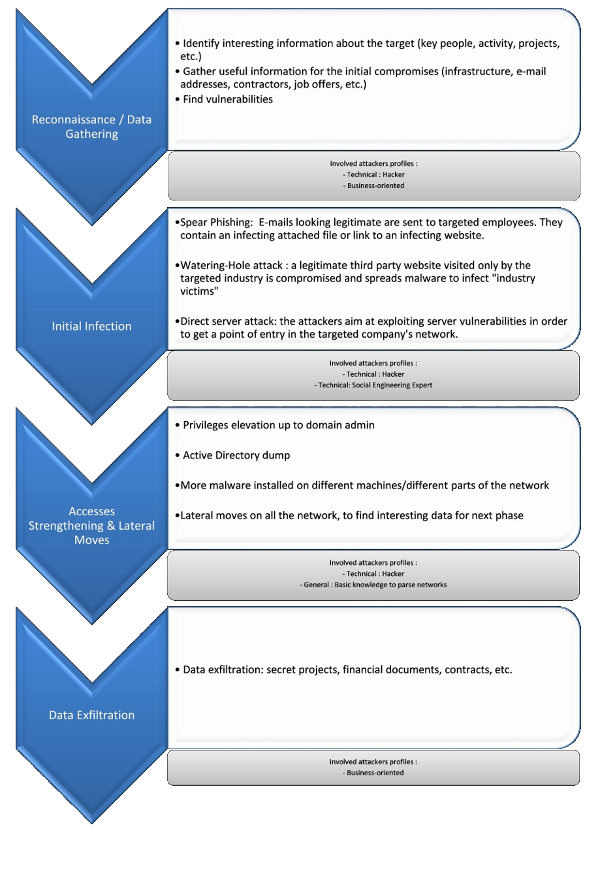
Our next blog post in this serie will cover the “reconnaissance” part, sometimes also called “data gathering” phase.


