Since October 24th, our Threat Intelligence team has been collecting many news related to a new family of ransomware named itself “BadRabbit.” This emerging threat seemingly first targeted institutions and companies in Russia and Ukraine, among them media group Interfax, Kiev’s metro system, and Odessa Airport. The ransomware spread towards other countries such as Bulgaria, Poland, Germany, Turkey and Japan. Some victims are also located in the US.
Back in August 2017, Security Service of Ukraine (SBU) first raised concerns about a possible future cyber-attack targeting Ukrainian institutions and companies, which suggests that this attack was set up for a long time ago.
What is Bad Rabbit?
How Bad Rabbit Ransomware works
BadRabbit is a ransomware that encrypts both user’s files and hard drive, restricting access to the infected machine until a ransom in Bitcoin is paid to unlock it. It also has spreading features through SMB protocol.
Reverse-engineering BadRabbit code raises many similarities with NotPetya ransomware. However, various elements let us think that both campaigns are not that similar in their objectives:
- The delivery method differs: while NotPetya was able to execute the malicious file directly on many computers, BadRabbit compromised specific websites to deliver its payload and required user interaction.
- So far, BadRabbit made some 200 victims, far less than the number of victims the NotPetya attack affected.
- Except for sabotage, motivations may not be the same.
BadRabbit has been tied by security researchers to various threat actors, among them BlackEnergy, but deeper investigations will be required in order to confirm this statement.
Technical Part
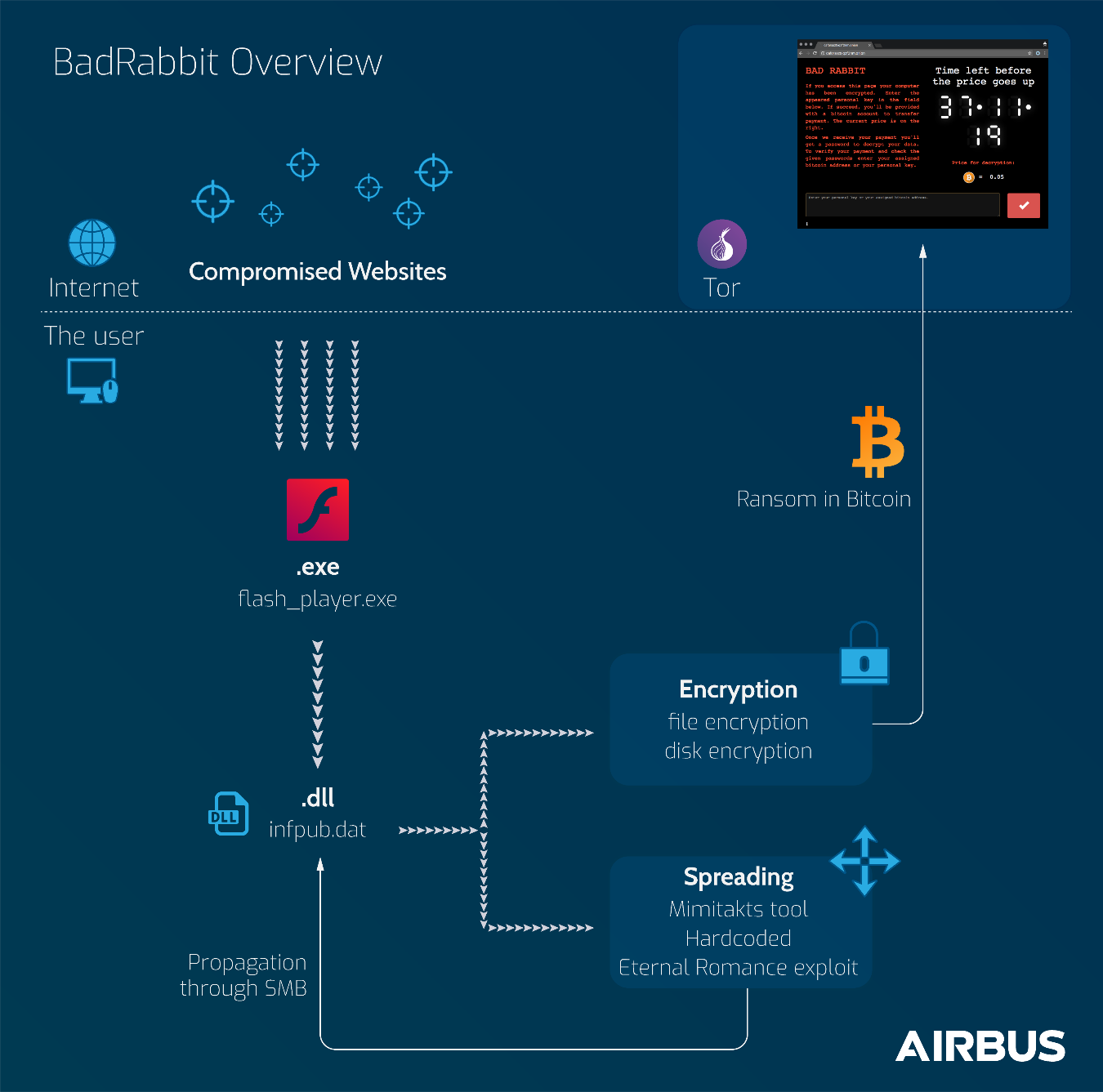
The primo infection is made through an executable download: some popular websites have been compromised to trick visitors into installing a fake flash player update.
For now, the ransom is set at 0.05 BTC (around $290), and is said to raise at a fixed timer.
Once installed the following actions occur on the infected machine:
- File encryption (list of impacted file extensions can be found below)
- Master Boot Record (MBR) encryption, blocking machine boot procedure
- Usage of the commom tool “Mimikatz” to harvest credentials that enables lateral movements in victims’ network.
- BadRabbit then tries to spread through SMB using different methods:
> using a hardcoded credential list
> using harvested credentials
> using Eternal Romance exploit
Is There a Bad Rabbit Ransomware Fix?
Quick and dirty ways to prevent the payload execution have been found by security researchers (2):
- Create the following files c:\windows\infpub.dat & c:\windows\cscc.dat
- remove ALL the inherited PERMISSIONS for the two files created above.
What is Bad Rabbit Targeting?
Impacted File Types
Bad Rabbit ransomware encrypts the following types of files:
.3ds.7z.accdb.ai.asm.asp.aspx.avhd.back.bak.bmp.brw.c.cab.cc.cer.cfg.conf.cpp.crt.cs.ctl.cxx.dbf.der.dib.disk.djvu.doc.docx.dwg.eml.fdb.gz.h.hdd.hpp.hxx.iso.java.jfif.jpe.jpeg.jpg.js.kdbx.key.mail.mdb.msg.nrg.odc.odf.odg.odi.odm.odp.ods.odt.ora.ost.ova.ovf.p12.p7b.p7c.pdf.pem.pfx.php.pmf.png.ppt.pptx.ps1.pst.pvi.py.pyc.pyw.qcow.qcow2.rar.rb.rtf.scm.sln.sql.tar.tib.tif.tiff.vb.vbox.vbs.vcb.vdi.vfd.vhd.vhdx.vmc.vmdk.vmsd.vmtm.vmx.vsdx.vsv.work.xls.xlsx.xml.xvd.zip
Hosts IOCs
|
Filename: Description: MD5: Sha1: Sha256: |
install_flash_player.exe Dropper fbbdc39af1139aebba4da004475e8839 de5c8d858e6e41da715dca1c019df0bfb92d32c0 630325cac09ac3fab908f903e3b00d0dadd5fdaa0875ed8496fcbb97a558d0da |
|
Filename: Description: MD5: Sha1: Sha256: |
infpub.dat Payload 1d724f95c61f1055f0d02c2154bbccd3 79116fe99f2b421c52ef64097f0f39b815b20907 579fd8a0385482fb4c789561a30b09f25671e86422f40ef5cca2036b28f99648 |
|
Filename: Description: MD5: Sha1: Sha256: |
cscc.dat Encryption driver (32-bits) b4e6d97dafd9224ed9a547d52c26ce02 59cd4907a438b8300a467cee1c6fc31135757039 682adcb55fe4649f7b22505a54a9dbc454b4090fc2bb84af7db5b0908f3b7806 |
|
Filename: Description: MD5: Sha1: Sha256: |
cscc.dat Encryption driver (64-bits) edb72f4a46c39452d1a5414f7d26454a 08f94684e83a27f2414f439975b7f8a6d61fc056 0b2f863f4119dc88a22cc97c0a136c88a0127cb026751303b045f7322a8972f6 |
|
Description: MD5: Sha1: Sha256: |
Mimikatz (64-bits) 347ac3b6b791054de3e5720a7144a977 413eba3973a15c1a6429d9f170f3e8287f98c21c 301b905eb98d8d6bb559c04bbda26628a942b2c4107c07a02e8f753bdcfe347c |
|
Description: MD5: Sha1: Sha256: |
Mimikatz (32-bits) 37945c44a897aa42a66adcab68f560e0 16605a4a29a101208457c47ebfde788487be788d 2f8c54f9fa8e47596a3beff0031f85360e56840c77f71c6a573ace6f46412035 |
|
Filename: Description: MD5: Sha1: Sha256: |
dispci.exe Decryptor b14d8faf7f0cbcfad051cefe5f39645f afeee8b4acff87bc469a6f0364a81ae5d60a2add 8ebc97e05c8e1073bda2efb6f4d00ad7e789260afa2c276f0c72740b838a0a93 |
Network IOCs
|
SMB |
shares |
admin atsvc browser eventlog lsarpc netlogon ntsvcs |
spoolss samr srvsvc scerpc svcctl wkssvc |
|
logins |
Administrator administrator Admin Guest User User1 user-1 Test root buh boss ftp Rdp Rdpuser rdpadmin |
manager support work other user operator backup asus ftpuser ftpadmin nas nasuser nasadmin superuser netguest alex |
|
|
passwords |
123456789 User user guest Admin 12345678 test123 adminTest 12345 123456 1234 1234567890 Administrator123 password Admin123 admin123Test123 user123 1234567 Guest guest123 User123 123 test root administrator123 |
Guest123 111111 Administrator administrator 123321 321 55555 777 77777 god love qwe qwe123 qwe321 qwer qwert qwerty qwerty123 secret sex uiop zxc zxc123 zxc321 zxcv |
Tor site on which the victim is asked to retrieve its decryption key:
[http://caforssztxqzf2nm[.]onion]
Prior to payload download, victim’s fingerprinting information are posted on this url: http://185.149.120[.]3/scholargoogle/. This IOC can be used for detection.
Distribution url from which the payload is downloaded by the victim. This url must be blocked to avoid infection:
hxxp://1dnscontrol[.]com/flash_install.php
Below is a list of compromised websites. These urls are not to block as is since they still are legitimate, however their requests should be closely monitored.
hxxp://argumentiru[.]com
hxxp://www.fontanka[.]ru
hxxp://grupovo[.]bg
hxxp://www.sinematurk[.]com
hxxp://www.aica.co[.]jp
hxxp://spbvoditel[.]ru
hxxp://argumenti[.]ru
hxxp://www.mediaport[.]ua
hxxp://blog.fontanka[.]ru
hxxp://an-crimea[.]ru
hxxp://www.t.ks[.]ua
hxxp://most-dnepr[.]info
hxxp://osvitaportal.com[.]ua
hxxp://www.otbrana[.]com
hxxp://calendar.fontanka[.]ru
hxxp://www.grupovo[.]bg
hxxp://www.pensionhotel[.]cz
hxxp://www.online812[.]ru
hxxp://www.imer[.]ro
hxxp://novayagazeta.spb[.]ru
hxxp://i24.com[.]ua
hxxp://bg.pensionhotel[.]com
hxxp://ankerch-crimea[.]ru
hxxp://Adblibri[.]ro
How Can Airbus CyberSecurity Help?
We prevent, protect, detect and respond to cyber threats of all sizes and types. Discover how we do this and learn more about our cyber security products and services today.


