At the S4X19 ICS Security Conference 2019 (14th -17th January 2019) Otis Alexander, Lead Cyber Security Engineer at MITRE, gave a first glimpse of the ATT&CK matrix focusing on Industrial Control Systems (ICS). One year later on the 7th of January 2020 MITRE released the initial official version of ATT&CK for ICS.
What is ATT&CK?
MITRE introduced the Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) in 2013 as a central knowledge base for adversary behaviour. It is based on real observations of cyber security incidents and maps the tactics, techniques and procedures (TTPs) to its knowledge base. TTPs are the “toughest” attack indicators regarding “The Pyramid of Pain”, as introduced by cyber security professional David J Bianco.
ATT&CK can be used for multiple use cases like adversary emulation and red teaming, SOC maturity assessment or cyber threat intelligence enrichment.
The framework categorises its information in tactics, techniques, mitigations, groups and software. Tactics can be seen as the phases of an attack. Each phase has a certain goal which the adversary tries to reach. Each tactic has certain techniques that represent how to achieve these goals. For every technique there are mitigations for how to protect the organisation. Adversaries use different types of software which are also represented in the framework. All of this information can be linked to groups which are traced by different security organisations.
Until the start of this year the ATT&CK matrices didn’t focus on the ICS world.
Why ATT&CK for ICS?
There are several motivations to introduce a separate ATT&CK matrix for ICS. First, adversaries pursue new goals in the ICS domain. The three generally accepted objectives of information security are represented by the Confidentiality, Integrity and Availability (CIA) triad, prioritising confidentiality ahead of the other two objectives. In ICS security, the priority is on the industrial process because the whole ICS environment is only build to keep the industrial process alive and running efficiently. Therefore, the availability and integrity are more important, leading to a change in goals for the attackers.
The second reason is that the ICS domain differs in defence and technology. The devices are often embedded platforms which use specialised process automation protocols and a great variety of ICS applications are operating. The difficulties in this environment are that security and data collection for security monitoring were not in focus when developing and integrating the devices and applications. Furthermore mitigations face unique concerns as asset owners´s priority isthe availability of the industrial process.
Finally, an attack on the ICS domain has specific consequences. On top of potential process and operation unavailability control over processes could be lost, leading to safety concerns.
Welcome ATT&CK for ICS
As a result MITRE introduced the ATT&CK for ICS matrix on 7th January 2020 (fig. 1), where new tactics, techniques, software and groups relevant to ICS are introduced. However, it also contains a new level of abstraction regarding assets. In the announcement, blog post Otis Alexander explains the reason for this. The ICS specific assets serve a consistent function regardless of the underlying operating system, hardware platform or application.
But how does ATT&CK for ICS interact with the existing domains?
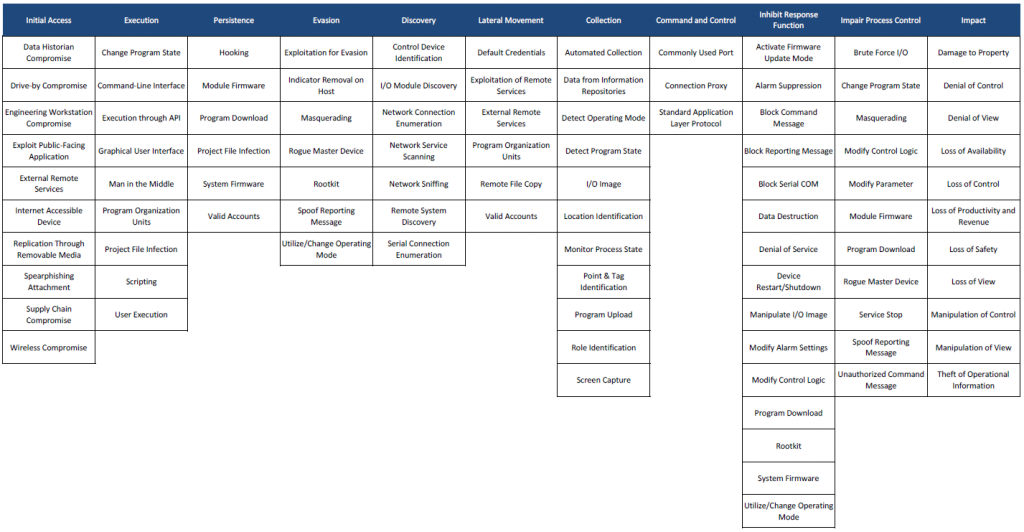
(Source: https://collaborate.mitre.org/attackics/index.php/Main_Page )
Enterprise and ICS – A friend in need is a friend indeed
Taking a closer look at the ATT&CK for ICS matrix, some techniques are already featured in the Enterprise matrix. Since the 1990s, when the Purdue Enterprise Reference Architecture (PERA) was developed, it is clear that Operational Technology (OT) has a direct connection to IT i.e. the enterprise network. Moreover, today’s business strategies like Industrial Internet of Things (IIoT) or Industry 4.0 are built on this connection.
Generally, one should take into account ATT&CK for Enterprise and treat the new ICS knowledge base rather as an extension to it, as described by Austin Scott from Dragos in his blog post. Indeed, the Entreprise Version has passed through many years of continual improvement from the MITRE community and very often adversaries enter the OT environment from the IT network.
Comparing ICS with Enterprise
However, some specific attack campaigns targeted ICS only, the most famous being Stuxnet. Mapping Stuxnet to the ATT&CK for ICS matrix, as shown in figure 3, quickly shows how complex this attack was. Business risk owners can now identify which techniques to focus on if they need to minimise the risk from strikes like Stuxnet.
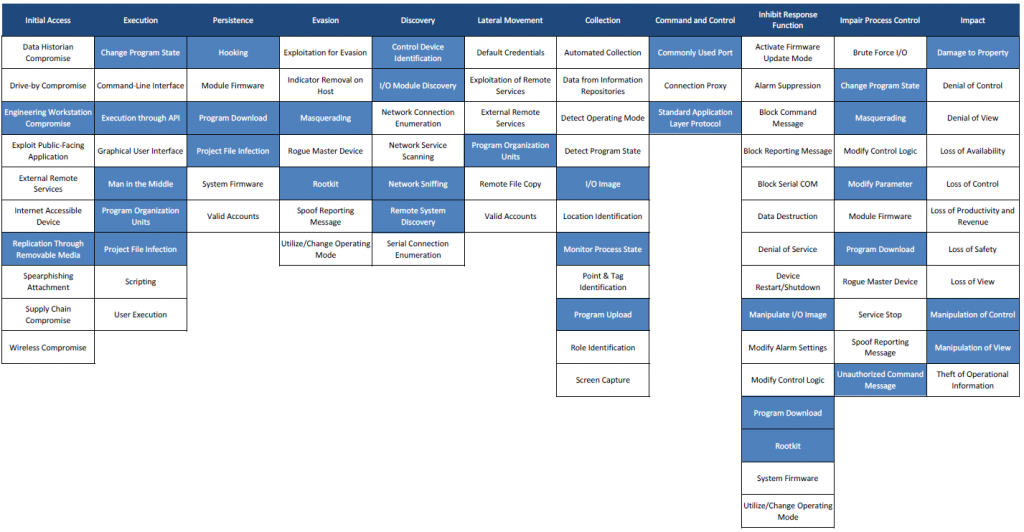
As ICS are part of the OT domain, not all incidents in OT are targeted on ICS only. Many adversary campaigns like WannaCry infect critical ICS by pivoting into the OT environment. Another example for adversary software that originates from the enterprise zone is Backdoor.Oldrea.
Backdoor.Oldrea also known as Havex is a Remote Access Trojan (RAT) used by Dragonfly. Dragonfly has been active since at least 2011. Backdoor.Oldrea is listed with ID S0093 in ATT&CK for Enterprise and ID S0003 in ATT&CK for ICS. As Dragonfly targets defence and aviation companies, the energy sector and other ICS relates companies, there is a lot of information available in both matrixes.
Backdoor.Oldrea uses several techniques in the industrial context which helps Dragonfly to gather information about devices in the network and allows the group to deploy other payloads with additional functionality. By comparing this RAT in both matrixes like in table 1, it is observable that there are no techniques used in both of them. Dragonfly used the software for different goals (tactics) in each environment. Therefore the threats which an organisation has to consider are different. By taking the threat perspective it’s absolutely reasonable to list Backdoor.Oldrea in both knowledge bases with different techniques.
| ATT&CK for ICS | ATT&CK for Enterprise |
|---|---|
| Role Identification (T850) | Credential Dumping (T1003) |
| Control Device Identification (T808) | Data Encrypted (T1022) |
| Remote System Discovery (T846) | Data Obfuscation (T1001) |
| Location Identification (T825) | Email Collection (T1114) |
| Denial of Service (T814) | File and Directory Discovery (T1083) |
| Supply Chain Compromise (T862) | File Deletion (T1107) |
| Spearphishing Attachment (T865) | Process Discovery (T1057) |
| Automated Collection (T802) | Process Injection (T1055) |
| User Execution (T863) | Registry Run Keys / Startup Folder (T1060) |
| Point & Tag Identification (T861) | System Information Discovery (T1082) |
| System Network Configuration Discovery (T1016) | |
| System Owner/User Discovery (T1033) |
Table 1: Comparison of used Techniques of Backdoor.Oldrea in ATT&CK for ICS and ATT&CK for Enterprise
Conclusion
Blue teams who have to protect IT and OT environments need the interaction of both Enterprise and ICS matrix depending on which threat should be addressed in which zone. ATT&CK for ICS is a great addition to the existing knowledge base and fills a large and important gap taking into account the assets present on Levels 0 to 2 of the PERA model.
ATT&CK for ICS is a community project. Before the initial release, more than 100 experts from 39 organisations helped MITRE to build this knowledge base. MITRE relies on the contribution from real incidents to improve its matrices.
All this knowledge is integrated in Airbus CyberSecurity’s IT and OT security portfolios and in particular our SOC4.0 services. Airbus SOC4.0 is a managed security service to monitor Information and Operational Technology (IT/OT) infrastructures, detect and prevent security incidents and cyber-attacks. More on SOC4.0 in our whitepaper here.
If you not only want to benefit from ATT&CK but also contribute, you can find more information here.
References:
Blog post: “Launching ATT&CK for ICS” by Otis Alexander – https://medium.com/mitre-attack/launching-attack-for-ics-2be4d2fb9b8
Blog post: “The Pyramid of Pain” by David J. Biaanco – http://detect-respond.blogspot.com/2013/03/the-pyramid-of-pain.html


