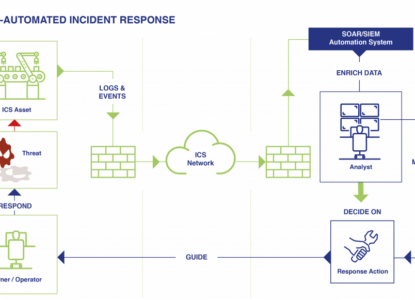
In an increasingly complex cyber threat landscape, effective crisis and SecOps management must be balanced between pre and post attack activities. It’s equally important to both test your organisation’s response capabilities and to invest in efficient recovery after an incident.
Currently experiencing an incident?
Call +33 9 72 30 13 99 if you’re in the UK or France, or request a call back from our German team.
Pre-attack: Understand your cyber resilience
It’s critical to understand your organisation’s capacity to respond to a cyber attack. Our expert team can help you achieve this through:
- Disaster and crisis management consulting: Disaster recovery planning, as well as advice and exercises for crisis management
- SecOps governance consulting: An assessment of your security operational capacities, enriched by our MSS SOC> experience
- RED and PURPLE team exercises: Test your cyber defence and SOC capacities by simulating real attacks, without informing your security team
Post-attack: Quickly recover from a cyber incident
During a cyber attack, time is of the essence.
To support customers at this difficult and often frightening time, we’ve built a Computer Security Incident Response Team (CSIRT). The team applies a tried and tested methodology to detect, contain and remove any threats from your systems:
First, diagnose the incident
- Identify the compromised systems
- Survey the initial attack vector
- Understand the attacker’s privilege level
- Investigate the attacker’s tools
- Identify the attacker’s means of communication
- Analyse the impact of the attack
- Create an incident timeline
- Produce a list of compromised equipment and systems, as well as malicious files
Then, eradicate the problem
- Report on the removal of the problem
- Offer recommendations for perimeter partitioning of the compromised area
- Suggest how to adapt filtering and detection rules
- Provide markers and IOC
- Harden recommendations
- Advise on the attack’s potential wider impacts
Thirdly, all-important reconstruction activities
- Restore the system to working order
- Reinstall infrastructure components
- Propose new security settings
- Consult on implementing robust cyber security policies and processes
Lastly, conduct further investigations to prevent an incident from reoccurring
- Analyse programs, logs, computers, and malware