This new version leaves the following message on the infected computers :
=============================================================================================================================================================================== BitCrypt v2.0 (bug fixed) =============================================================================================================================================================================== English Attention!!! All necessary files on your PC ( photos, documents, data bases and other) were encoded with a unique RSA-1024 key. Decoding of your files is only possible by a special programm that is unique for each BitCrypt ID. Specialists from computer repair services and anti-virus labs won't be able to help you. In order to receive the program decryptor you need to follow this link http://www.bitcrypt.cc and read the instructions. If current link doesn't work but you need to restore files please follow the directions: 1. Try to open link kphijmuo2x5expag.tor2web.com. If you failed proceed to step 2. 2. Download and install tor browser http://www.torproject.org/projects/torbrowser.html. 3. After installation, start tor browser and put in the following address kphijmuo2x5expag.onion Remember, the faster you act the more chances to recover your files undamaged. ===============================================================================================================================================================================
After this message, the same message follows, written in several languages: french, german, russian, italian, spanish, portugese, japanese, chinese and arabic.
The new version of the malware has been analyzed and revealed that the ransomware was indeed using real RSA-1024, making it impossible for us to break it.
It took about a week to the Bitcrypt authors to update the code, correct their mistake, spread their message in more languages, and keep their business running.
Should we keep this info secret ? Some people would have preferred us to disclose the weakness on a restricted community. Well, in this case, our guess is that it wouldn’t have helped as much victims as it did. Is there really a good answer anyway for this question ?
Seeing how fast the bug got corrected, we wondered how juicy this fraud was, and started looking at the financial trails left by this particular ransomware. Other researchers already published intel about other ransomware : Michele Spagnuolo studied the CryptoLocker ransomware bitcoin trails in a very interesting thesis. With this thesis, Michele released his BitIodine tool (in collaboration with Stefano Zanero and Federico Maggi) which helps following money trails on bitcoin. They discovered that CryptoLocker was making great profits: 771 ransoms paid in about 4 months, for a total of 1 100 000 dollars. DELL SecureWorks also published information about it here.
Now back to BitCrypt.
This ransomware offers different ways to pay the ransoms : Bitcoin payment, MoneyGram or Western Union money transfer.
Bitcrypt’s ransom has been changing through time: sometimes 0.4 BTC, sometimes 0.2 BTC, then 0.5 BTC, then 0.4 again … My guess is that it raised to 0.5 just after Bitcoin lost value (due to Mt.Gox’s bankruptcy). When it climbed again, the cybercriminals lowered once again the ransom to 0.4 BTC.
Working with Michele Spagnuolo and Stefano Zanero (thank you very much for your help !), we could analyze the payments done to the known Bitcoin hashes used by the cybercriminals, during a period covering the 5th of february 2014 (date of appearance of this new threat) to the 21st of March 2014.
During this period, there have been 164 ransoms paid, for a total of 46,877971 BTC (about 21 270 dollars at the time of writing).
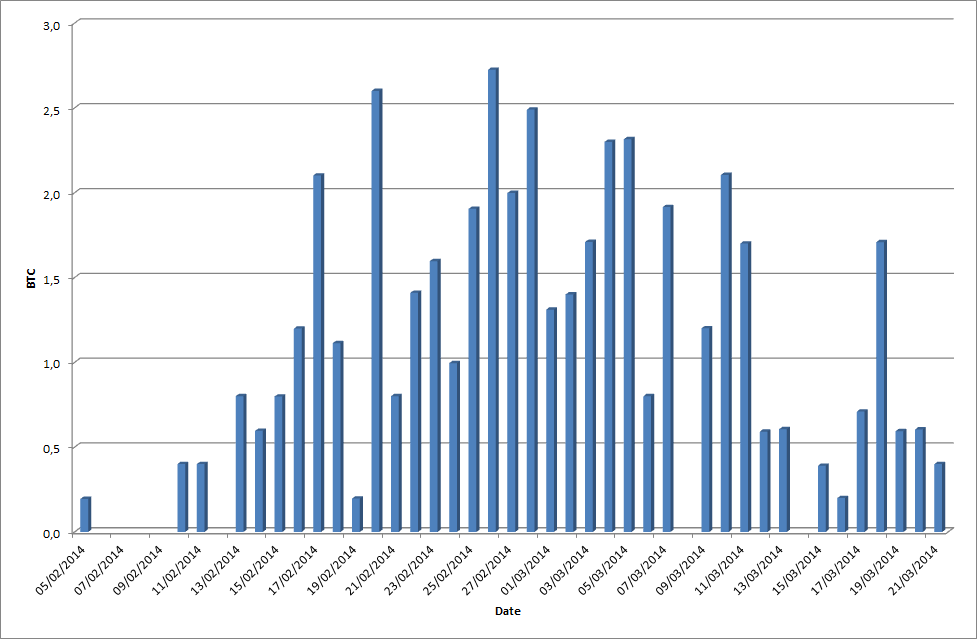
As you can see on this graphical representation, there is an amount of payments of the ransom varying between 0 and 10 each day.
One might think this is a very lucrative activity for someone. Yet the cybercriminals rarely work alone, and have to share the profits. 21 000 dollars a month (roughly) sounds like a good salary, yet if there are 10 people working on it, the profit is greatly reduced.
Pushing our investigation further, we decided to act innocent and send a message to the fraudsters, pretending to be a victim who does not understand Bitcoin. The fraudsters answered within ten minutes telling us the only alternatives were to pay via MoneyGram or Western Union (300 $).
The money the fraudsters might get via MoneyGram or Western Union is unknown, yet our experience tells us that it must be very limited and close to zero.
As a side note, the Bitcrypt guys mention how important it is to say your country in the message, when you reach them. We reached them from different countries and it did not change anything regarding the ways to pay the ransom : always Bitcoin/MoneyGram/Western Union.
The e-mail address used by that team is bitcryptcc@gmail.com. We were also able to obtain the identity of the person collecting the money when Wester Union payment is chosen by the victim :
Reciever Frst Name: Oleh
Reciever Last Name: Chabanenko
Reciever City: Odessa
Reciever Country: Ukraine
This is probably what we call a “money mule” : a person who receives the money, keeps a % of it (less than 10%), and sends the rest to the real cybercriminals, or to another ring of mules.
This has been confirmed by the fraudster after some social engineering, in bad english :
“I do not Oleh 🙂 And I’m not from Ukraine.”
As a funny sidenote, it should also be mentioned that when asked, the fraudsters reduces the ransom from 300$ to 250$:
“We can make a small discount for you if you will make the payment in 48 hours”
With a bit more social engineering, we offered fake delivering services to the fraudsters, to see how they reacted. The goal was to confirm they were a group and not an individual, and know a bit more about their methods. Soon enough, they offered us a partnership:
“we can offer you a different way of working. We will give you the exe file of the virus with your personal prefix and Bitcoin wallet. All that will be received on this purse divide 50/50”
So, we can make the assumption that there might be several people using BitCrypt 2 in the wild. This is unconfirmed yet, as we did not find any other Bitcrypt wallet provided at the infecting time.
Recently, Trend Micro blogged about BitCrypt now being dropped on systems together with the FAREIT malware, which steals several virtual currencies (Bitcoin, Electrum, MultiBit).
This ends our little journey in the BitCrypt world.
From our point of view, this ransomware does not generate enough profit for the fraudsters in the way they handle it. They must think the same, since they now decide to steal bitcoins from infected machines in addition to asking for a ransom.
As for defense against that kind of malware, there is only one thing to do: make regular backups of all your important data, be it in the cloud or locally on an external hard drive, only connected at backup time. Also, protect your virtual currencies (if you have some) by placing them on offline saving wallets.
Also, I would like to thank Fabien Perigaud for the time he spent with me on Bitcrypt 2.


