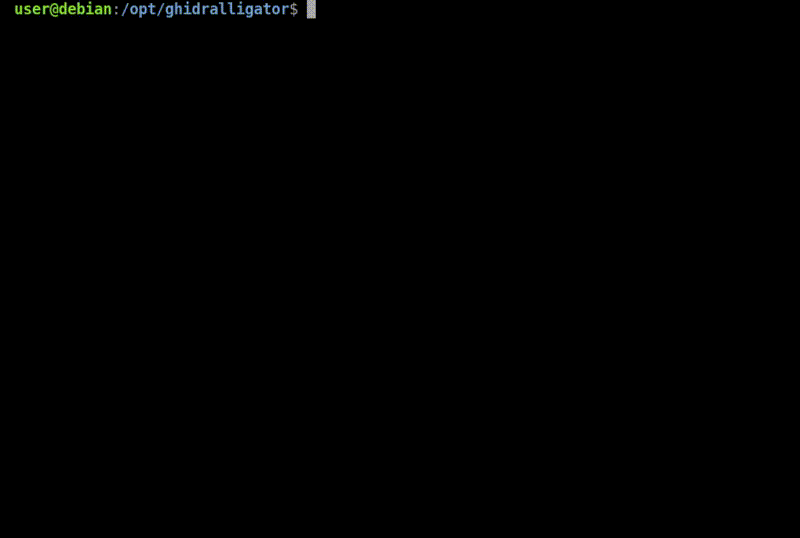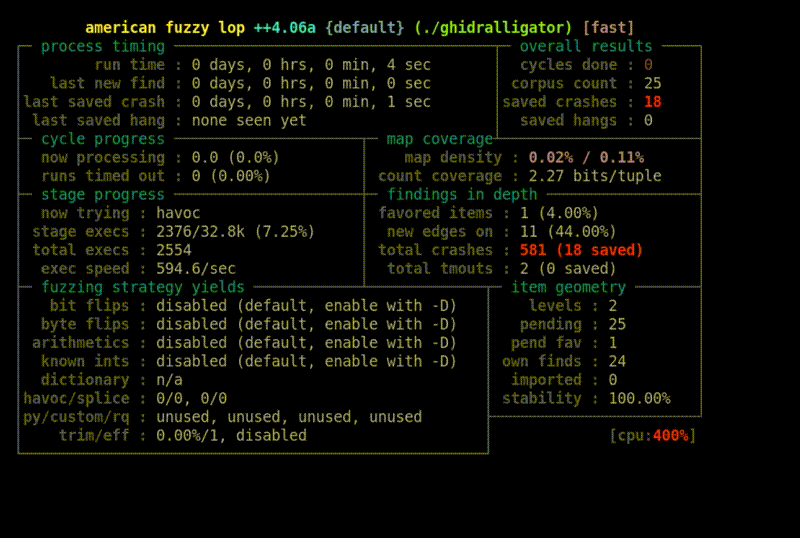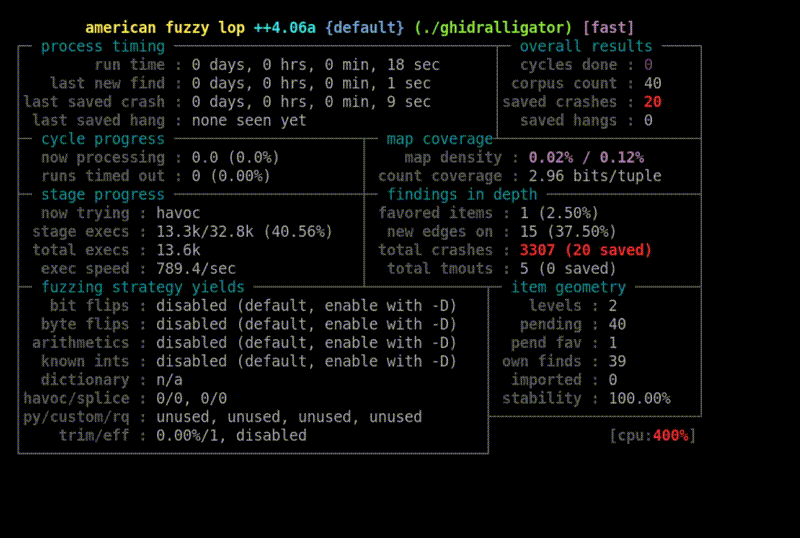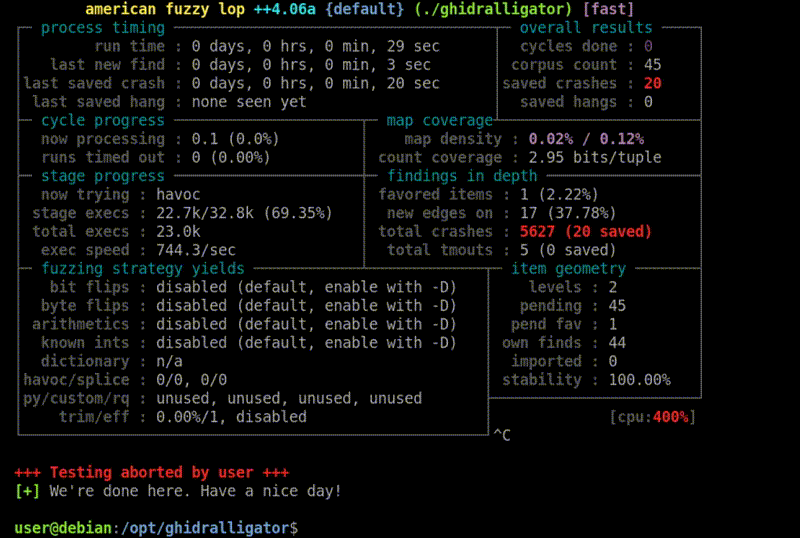
Fuzzing is one of the most favoured techniques used by researchers to discover vulnerabilities.
In this article, we introduce Ghidralligator, a newly designed tool. Ghidralligator is an emulator built upon Ghidra, capable of emulating a wide range of CPU architectures. Additionally, it can be integrated with AFL to enable snapshot fuzzing with code coverage functionality. Ghidralligator serves as the successor to afl_ghidra_emu.
For a comprehensive understanding of afl_ghidra_emu and fuzzing with code coverage, we recommend reading our previous article.
Ghidra Internals
Ghidra is a reverse engineering tool, developed by the NSA and released in 2019. It supports numerous CPU architectures. In afl_ghidra_emu, we utilised Ghidra’s emulation features. However, we encountered subpar performance due to Ghidra being substantial software primarily designed in Java, which is not optimised for the best possible emulation performance.
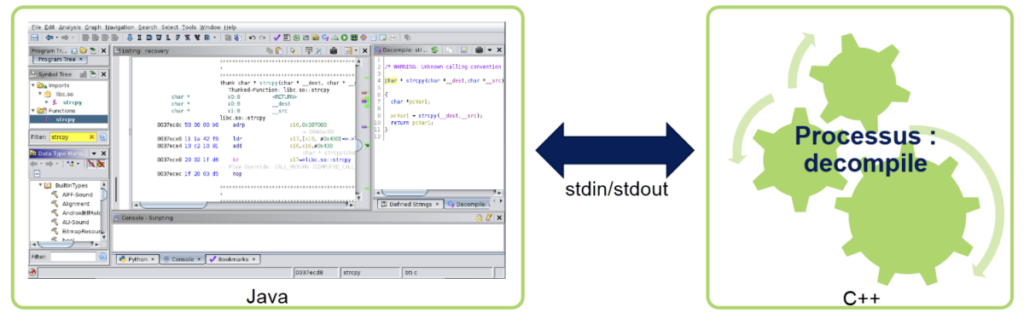
By delving deeper into Ghidra, we can identify two main components:
– The HMI (Human-Machine Interface), which is designed in Java.
– The decompile process, which is designed in C++.
The decompile process handles low-level tasks such as disassembly and decompilation. The HMI communicates with the decompile process through stdin/stdout.
As a result, the C++ source code for the decompile component can be re-used in another project for tasks such as disassembly, decompilation, and emulation!
In Ghidra, this C++ source code is referred to as libsla. Additional information can be found in Guillaume Valadon’s talk (in French).
Ghidralligator
Ghidralligator is developed in C++ and is based on the Ghidra libsla. Compared to afl_ghidra_emu, it offers significantly improved execution speed.
Ghidralligator leverages the intermediate language PCODE to achieve independence from CPU architectures. As a result, it can emulate any architecture supported by Ghidra.
Here are the features of Ghidralligator:
– Integration with AFL for code coverage analysis.
– Snapshot fuzzing.
– Detection of heap corruption issues such as out-of-bounds read/write operations, use-after-free, double-free, reading uninitialised memory, and read/write/execute access violations.
– CPU architecture independence.
Ghidralligator can be downloaded at https://github.com/airbus-cyber/ghidralligator.